Overview
- HOME
- Overview
We aim to realize a unified TEE architecture that can flexibly operate across diverse platforms ranging from IoT devices to the cloud. This architecture will allow the selection of appropriate enclave configurations and protection mechanisms according to specific requirements and threat models, while taking into account trade-offs among security, performance, and energy consumption.
From the hardware perspective, we will provide highly versatile TEE primitives. Using these primitives, system software will be able to flexibly configure protection domains. From the theoretical perspective, we will develop formal verification techniques to ensure that the protection domains built on top of the TEE primitives are provably secure against the assumed threat models.
Furthermore, we will develop a software environment that enables secure execution of advanced cryptographic operations on the proposed TEE. As a proof of concept (PoC), we will prototype applications that realize secure data distribution.
All developed artifacts will be released as open source including hardware IPs.
TEE and Its Issues
As shown in Table 1, each vendor provides its own protection model tailored to the typical requirements and threat models of its platform.
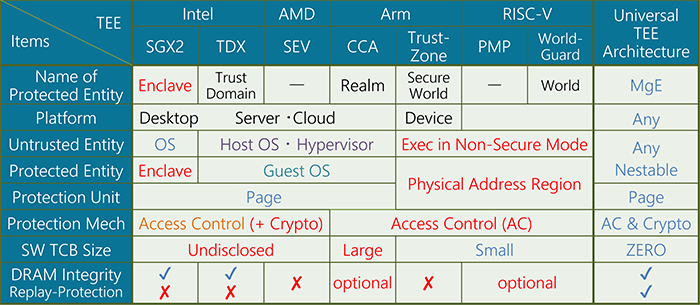
Intel SGX primarily targets servers and desktops, where part of a process’s memory region is designated as an enclave. Within this enclave, application code and data are protected from an untrusted operating system. The earlier version of SGX supported integrity assurance against memory side-channel attacks with an integrity tree. However, the later version, along with most other TEEs, do not support an integrity tree probably for performance reasons.
Arm TrustZone partitions a device into two execution environments, referred to as the secure world and the non-secure world. It protects the code and data executed in the secure world, including applications and a trusted OS, from access by applications and operating systems running in the non-secure world, primarily through hardware-enforced access control.
More recently, technologies such as AMD SEV, Intel TDX, and Arm CCA have drawn attention in server and cloud environments, focusing on protecting virtual machines (guest OSes) from untrusted hypervisors.
As shown above, hardware vendors provide proprietary protection models, leading to the following issues:
- Limited portability: Software built for one TEE hardware is difficult to port to another, as the differences are deeper than ISA-level and cannot be solved by recompilation from source codes.
- Threat model mismatch: If the system designer’s threat model differs from that assumed by the TEE hardware, the required level of protection may not be achieved, making the TEE effectively unusable.
Universal TEE Architecture
To overcome the above-described issues, we aim to realize the Universal TEE Architecture (UTA) that is designed to be single, flexible, and formally secure, where a TEE architecture refers to the combined design specification of both TEE hardware and system software:
- Single and Flexible: Although the architecture is unified, it can still provide appropriate protection models adapted to specific requirements and threat models, balancing tradeoffs among security, performance, and energy consumption.
- Formally Secure: By exploiting the unified architecture, this project develops formal verification methods that guarantee any protection model selected by the user satisfies the required security properties.
The realization of such a UTA is expected to bring the following benefits:
- Compatibility with existing TEEs, which expands the range of options available to current users.
- Broader adoption among potential users, since TEEs can be aligned with their specific requirements and threat models.
- Improved overall security through compliance with a single TEE architecture, which would centralize resources and strengthen security at the societal level, as already practiced in cryptography with AES and other widely adopted standards.